Cellular communication is the most stable wide-area wireless technology available today. The technology uses reserved frequency bands and commercial, well-maintained infrastructure. Having said that, there are several scenarios where your devices can experience connectivity issues. For example:
- The wireless module does not support the parameters of a specific network.
- The sequence of AT-commands is not optimal to establish a data connection under varying radio conditions.
- A mobile network whose signal is the strongest has issues such as uplink interference or core network outages.
Instead of relying on only one network in a country, EMnify global IoT SIM cards always use multiple networks, increasing the connectivity availability. Nevertheless, as outlined above there are still reasons for why devices may not be able to send data. In this post, you will learn about five functionalities that will help you detect and solve connectivity issues in real-time:
- Detect Issues: Event Alerts
- Detect Issues: Data volumes and device status
- Understand Issues: Network Events
- Resolve Issues: Network Reset
- Resolve Issues: Network Blacklisting
Event alerts
Log in to the EMnify Portal and check the Dashboard. Click on the tab EVENTS.
You will see all the network events related to your SIM cards and organization. By clicking on the severity, you can filter for all warning and critical events that have an impact on the connectivity.
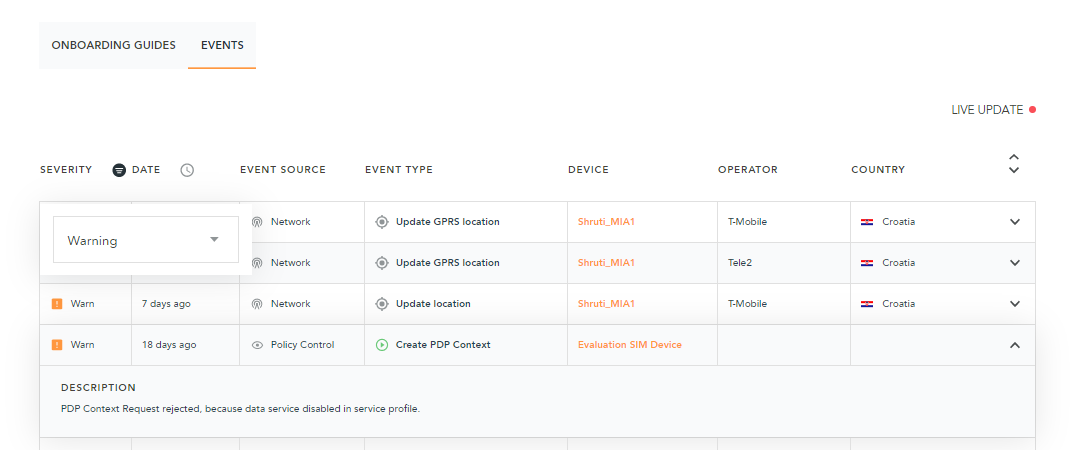
You can then proactively see which devices have identifiable connectivity issues. When clicking on the event, you will find a description that specifies the typical root cause of the issue and how it can be solved.
Real-time data volumes and device status
In case you have a specific device that is troublesome you can log in to the EMnify Portal and go to Connected Devices, then search for your device via ICCID, IMEI, or Name and click on detail.
The device status shows a simple categorization of the current connectivity state.
Blocked: The device has been blocked due to device policies (e.g. that the volume limit is reached). You can unblock the device by changing the policies.
Attached: The device has done a registration and location update with the network in the past. It can send and receive SMS in this state, but cannot establish a data session. This could be due to the wrong APN setting or roaming misconfiguration. Note that the device stays in Attached status even if it is powered off because the device does not notify the home network when turning off.
Online: The device currently has a data session
Offline: The device is no longer attached to a network and has not been trying to connect to a network for 24-48 hours.
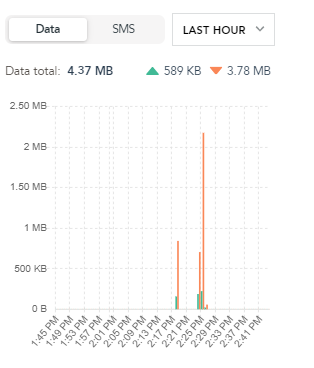
The next thing you can check is data statistics on device details. For example, if your sensor sends data every 15 mins you will be able to see when it sends the data for the last time.
Understand issues with network events
A device will always use the same event sequence to establish a data connection - in the following order:
- Update location - meaning that the device has registered and/or updated its location on the signaling network.
- Update GPRS location - meaning that the device has registered and/or updated its location on the data network.
- Create PDP context - meaning the device has established a data session.
- Delete PDP context - meaning the device has disconnected the data session.
Update location and update GRPS location can also happen multiple times before a data session / PDP context is created. When any of these events is rejected, this indicates a connectivity problem that can either fix itself or in some cases, needs intervention. You can filter for warning and critical events and see how to resolve the problem in the event description by clicking on the event.
Ensure that the events are happening in the frequency that you expect them to happen. For example, if your device firmware is configured to register and send data over a network every hour, you can check the actual behavior in the events.
Other problems that do not have a root cause in the network but in the device can also be diagnosed by looking at the events and their timestamps. Let's take a look at the following scenarios.
Scenario 1: Many location updates in a short timeframe without PDP context creation
This indicates that the device commands to register to a network (AT+COPS) are executed too frequently. The registration procedure can take anything from seconds to a couple of minutes and during that time no re-registration request should be done.
Scenario 2: Normal location and GPRS location updates but no PDP context creation
Change the APN setting to "em" or "emnify".
Scenario 3: PDP context created and deleted but no data transmitted:
You can check the volume sent over the data session in the PDP deletion event. For NB-IoT and LTE-M devices this behavior can happen when the device automatically connects to any network - rather specify the network to be used with the `AT+COPS` command in the device. Verify that the network is on EMnify's NB-IoT or LTE-M coverage map.
This can also indicate some errors in the command to establish the PDP, e.g. AT+QIACT (a Quectel specific command) instead of using AT+CGACT.
Resolve issues: Network reset
There are many reasons why connection issues arise. For example:
- The device executes the wrong procedures due to a bad firmware update.
- The device executes network registration too frequently that the network no longer allows it to register.
- You have simply changed a policy due to a blocked device.
To do a network reset, you need to go to Connected Devices, then search for the device and click on the network reset button. 
You can also reset the connectivity on multiple devices simultaneously. To do so, select devices on the Connected Devices overview page, and click on RESET in the top action bar:
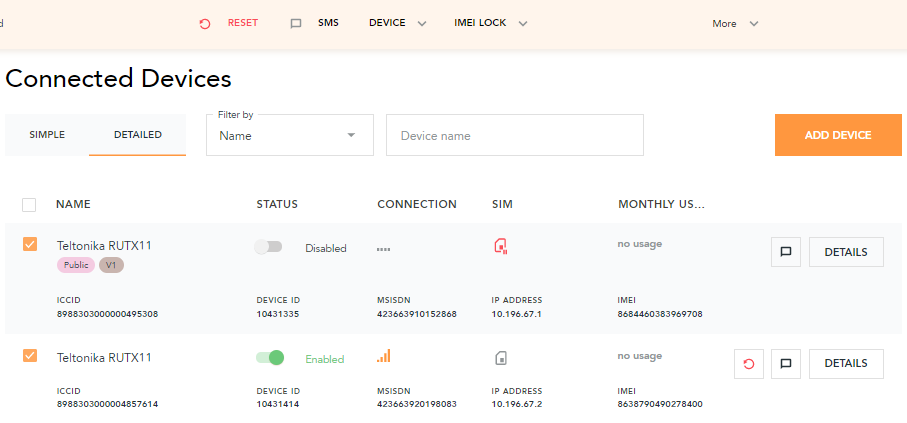
Resolve issues: Network blacklisting
There are several reasons why devices may not be able to register or establish a data session over a specific network:
- The module firmware does not support specific network parameters.
- The network or base station of a specific operator has been upgraded and is faulty, meaning devices are allowed to attach but can not establish a data connection.
- Devices can attach to the network because of good downlink quality, but the uplink quality is too poor to send data.
In these cases, it is possible to block the problematic mobile network so devices can no longer register with this network. The device will then automatically use a different network, which can resolve the connectivity issue.
To blacklist a network for a specific device you can go within the EMnify Portal to Connected Devices, then search for the device (ICCID, IMEI, etc.). Next, go to Details and add an operator to the Operator Blacklist. 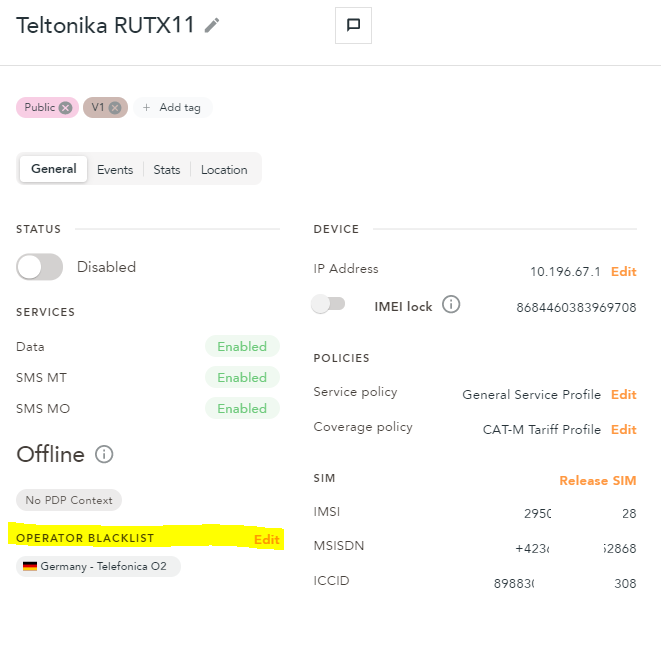
Alternatively, you can block a network on multiple devices using the bulk action on the EMnify Portal. To do so, select devices on the Connected Devices overview page and find the Blacklist Operators option in the top action bar:
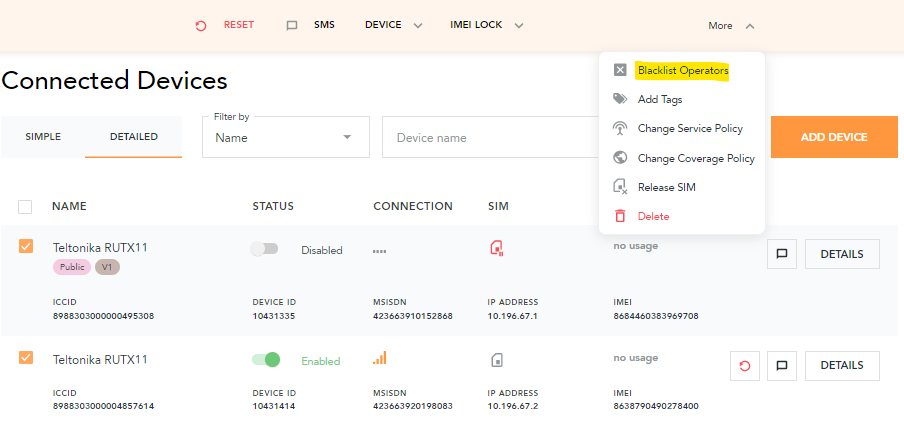
Summary
While cellular connectivity is the most stable and secure wireless technology available, with thousands of devices in the field, you need to be able to detect and fix even very infrequent issues. We presented five mechanisms that will help you to recover devices from connectivity issues.

Christian Henke
If you want to understand how emnify customers are using the platform Christian has the insights. With a clear vision to build the most reliable and secure cellular network that can be controlled by IoT businesses Christian is leading the emnify product network team.