
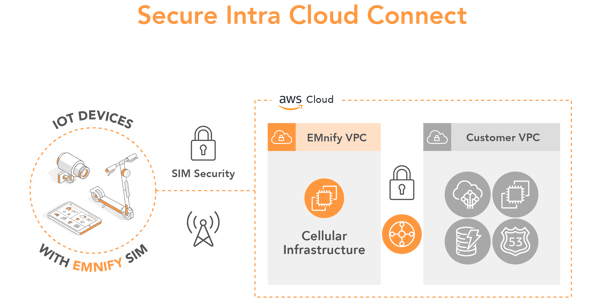
Connect devices securely to AWS VPC without using public Internet
emnify is a cellular cloud provider and the mobile network and management platform resides on AWS. Based on this, emnify already secures the data path up to AWS and customers with application servers on AWS can have a secure connection to their device by directly peering their VPCs with the one from emnify.
How the integration looks like
Prerequisites
The setup of Cloud Connect with the Transit Gateway attachment requires:
- device with an active emnify SIM
- the device sends data to application in VPC/EC2 instance (e.g. Python, Node.js, Java application / MQTT broker)
- in the emnify Portal, the service profile of the device has a local breakout configured to have the same region as the application server (can be configured during setup steps below)
- the EC2 instances should be launched in a /22 subnet or smaller. Larger CIDRs are not accepted by the emnify Portal and some subnets are not available.
Benefits
- devices and the application infrastructure reside within the same private network
- remotely access devices from AWS infrastructure via telnet / SSH
- device data does not traverse public internet
- VPC / EC2 instances do not need public IP
- fully scalable and managed AWS service
Remarks:
The secure connection is associated with a specific VPC - for example when hosting an own MQTT server or utilizing a VM for remote access. When only ASW IoT is intended to be used - a separate guide is provided in the AWS IoT Core setup page.
Configuration Steps
The following steps illustrate how to create an attachment using Cloud Connect to peer with your VPC. If you prefer video How-to's, check out our Youtube version here (Note: we only showcase one emnify's IP range in this video).
- In the emnify platform, navigate to the Integrations page. In the Secure Connections panel, click Add Secure Connections:
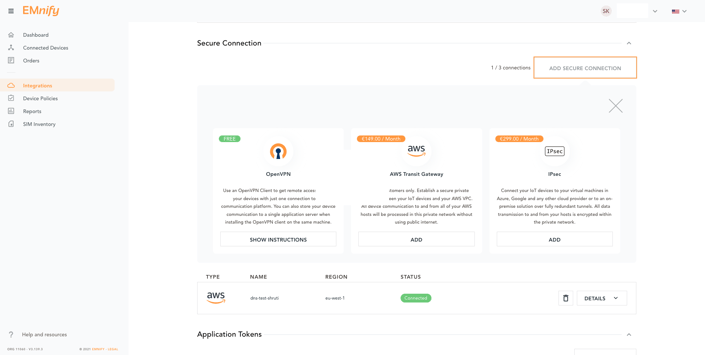
- Select Transit Gateway as the attachment type:
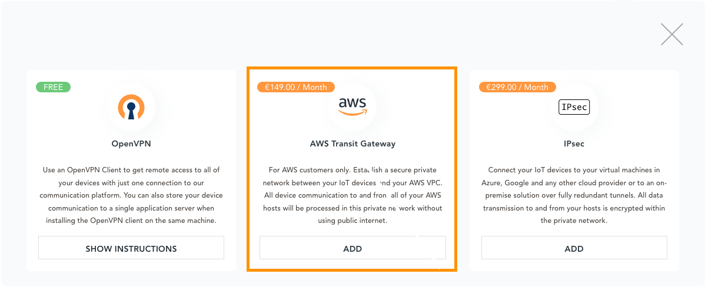
- Enter the destination account details and private CIDRs addresses. The CIDRs should be existing VPC or subnet IPV4 address ranges with a prefix between /32 and /22. If the IP address range is already taken you will be prompted to select a new one:
NOTE: the CIDR range 10.100.x.x is used internally by emnify and is therefore unavailable.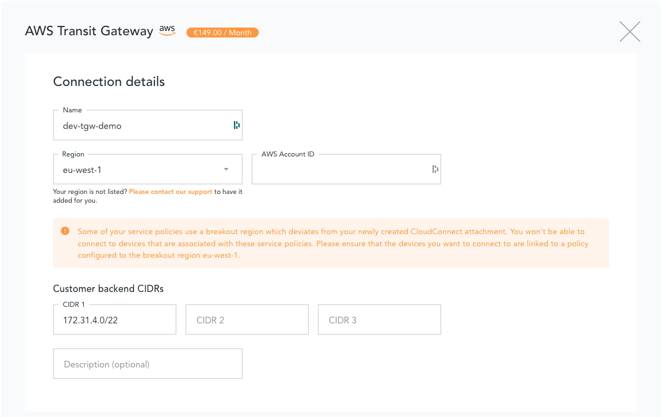
NOTE: Once the attachment is created, you will be billed at the end of the month as notified when creating the CloudConnect request
- In the AWS console, accept the pending resource share in Resource Share Manager. This step might not be necessary if you have already created CloudConnect attachments via Transit Gateway before.
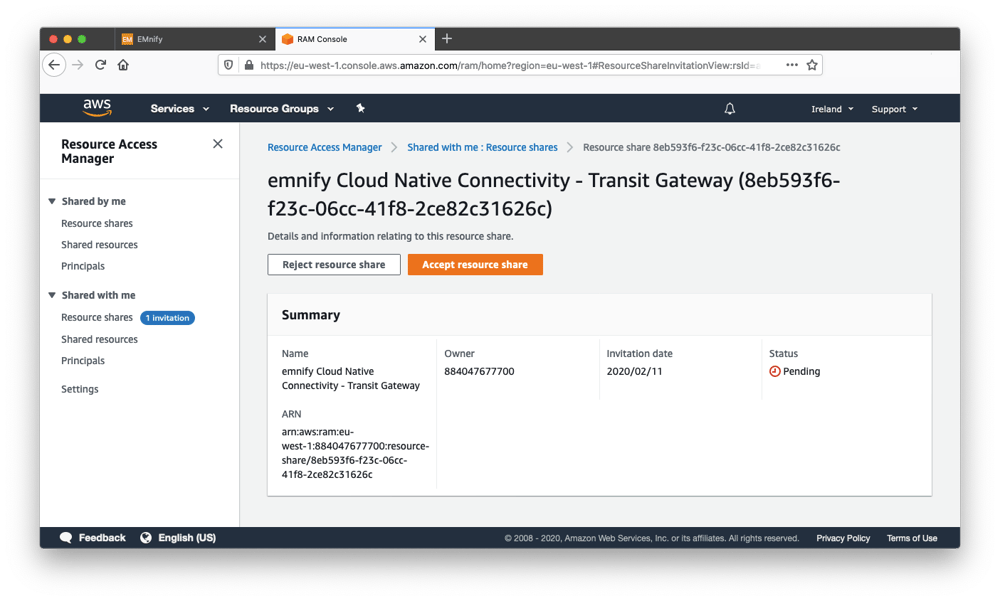
Once you have accepted the Transit Gateway resource share the emnify communication platform will automatically provision the private network interconnection through the TGW. This may take a couple of minutes - in which you can already proceed with configuring your side of the connection. - In the VPC dashboard, scroll down to Transit Gateways and select Transit Gateway Attachments (ensuring you are in the correct region as specified in the previous steps). Create a Transit Gateway Attachment and attach the VPC where the Application Servers are located to the shared Transit Gateway. During the process, the Transit Gateway can be configured to attach to one or multiple subnets of the VPC.
Note: The Transit Gateway ID is the Resource ID.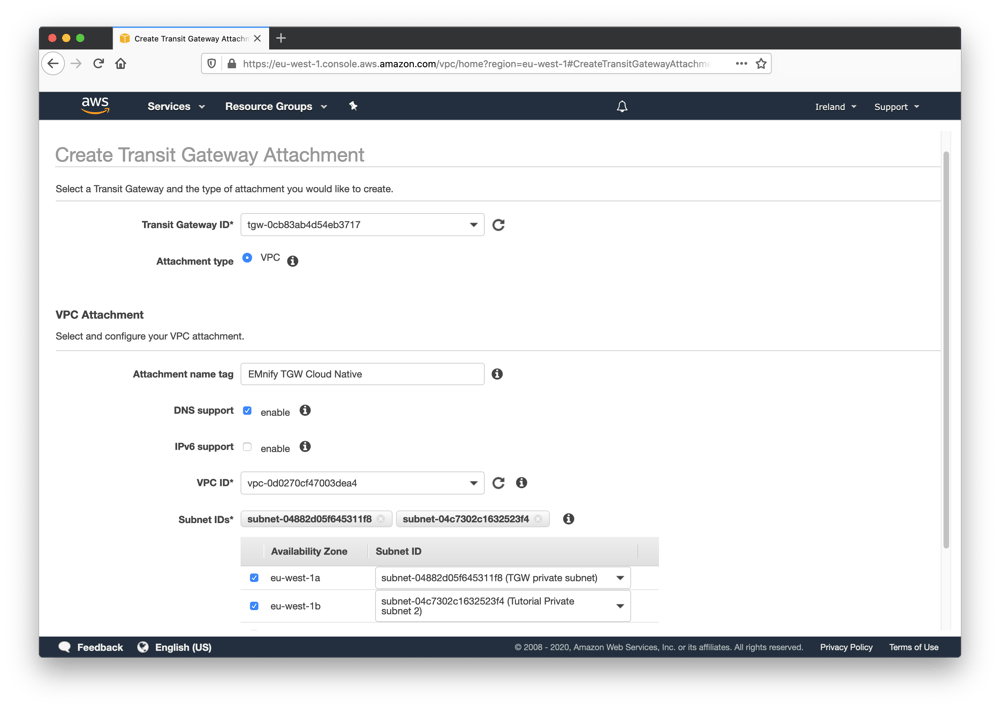
-
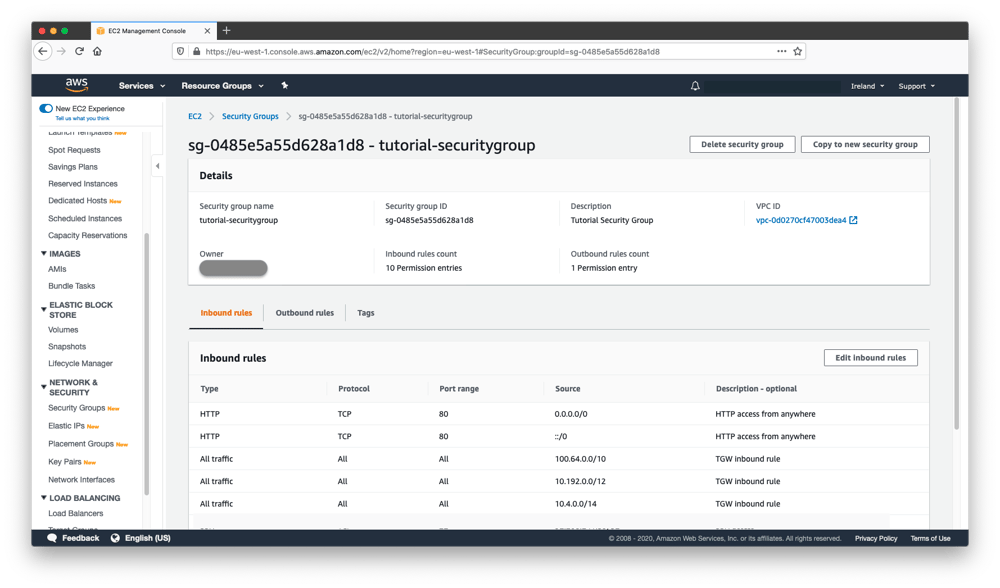
The final steps for setup is to configure the VPC Routing Table and the Security Group to allow routing data through the transit gateway.
In the VPC dashboard, navigate to Route Tables and edit the routes that are used by your application server. Click Add Route and emnify's IP ranges 10.192.0.0/12, 100.64.0.0/10, 10.112.0.0/12, 10.176.0.0/12 (to allow traffic from any of your IP ranges assigned to your account) and select the newly-created Transit Gateway as the target. -
Tip: an explanation of these route tables and how they should be configured can be found in the AWS documentation for Route Tables.
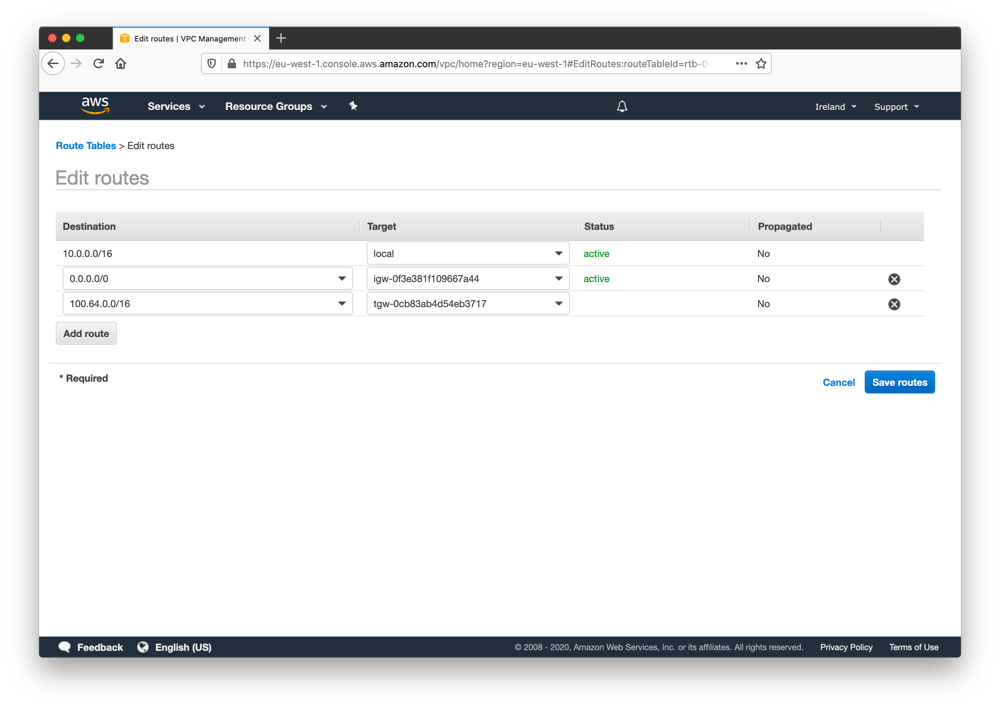
- Existing security groups need to be updated or you may create a new security which allow traffic from the transit gateway. A good security practice would be to limit the inbound and outbound rules of the security groups to only the ports and protocols that your application is using. Exactly which ports and protocols will depend on the use case and the type of application you are running in your VPC.
Verifying the attachment
If everything is correctly configured, the Cloud Connect panel in the emnify portal will show Active. In case the Transit Gateway is in a pending state (waiting on AWS or emnify) then please wait a couple of minutes until the provisioning is complete.
If the state says "Pending Customer Action" then return to step 5 to accept the Resource share.
Some basic connectivity checks can be performed using the ping network utility. The static private IP address of a device Endpoint is visible within the emnify portal, so given an example IP address of 1.2.3.4 and that the Endpoint is showing online (has an active PDP context), the following check can be performed:
- A response is expected from an EC2 instance within your VPC toward the emnify device IP:
PING 1.2.3.4PING 1.2.3.4: 56 data bytes64 bytes from 1.2.3.4: icmp_seq=0 ttl=56 time=16.225 ms
...
.jpg)
Jean-Eudes Ambroise
Director of Customer Success at emnify, Jean-Eudes is an expert in IoT.