
Security in the world of IoT is a hot topic. Although a combination of different security protocols is necessary to ensure data protection (e.g., firewalls, compliance engines, etc), securing the information as it travels over the internet should be a top priority. A Virtual Private Network, or VPN, is a technology that creates a secure network within the internet to which users and M2M/IoT devices (or endpoints) are connected. Without a VPN, data is transferred openly through the public internet, and is susceptible to security violations such as eavesdropping, information leakage and hacking. By using a VPN, you are contributing greatly to the safe and reliable operation of M2M and IoT connected devices.
In this blog post, we will explore the security advantages and the possibilities of transparent network access by implementing a VPN, walk you through the details of 3 different VPN clients, and give you our recommendations for implementing the right VPN. emnify strongly recommends the use of a VPN for all its customers, as well as the general public, and shares other security measures that can help keep you and your data safe.
Security
As soon as you connect an IoT device to the public internet, it is susceptible to viruses, malicious programs and hackers. The information you send and receive via the internet is open to being read or even altered.
A VPN provides a secure connection between a user and an IoT device. Even when data being transferred between you and a device is “sniffed” by a third party, encrypted VPN data only appears as incomprehensible characters. Data in this form would take a great deal of time and resources to decrypt, making it unlikely for anyone to do so. Also, when you and IoT devices communicate through VPN, your geographical locations are hidden from view.
A robust security system is not complete with a VPN alone. Other security measures you should consider as part of a comprehensive solution include:
- Hardware security (e.g., device security, embedded SIM options)
- Data oversight (e.g., creating SIM data caps, geographical SIM roaming caps)
- Software (e.g., Antivirus, secure cloud storage)
Limited Computing Power: Why VPN is Optimal for IoT Devices
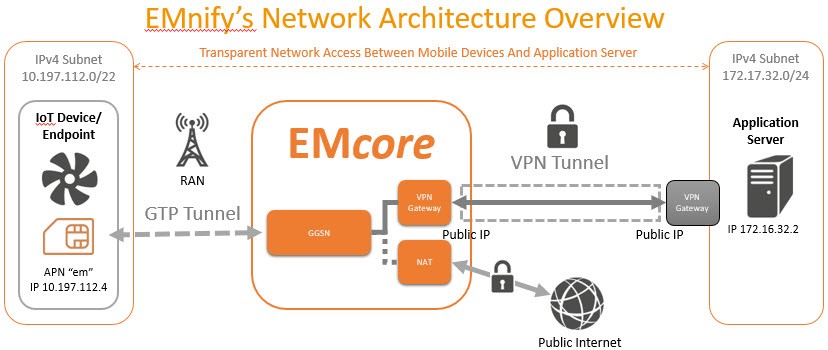
IoT devices are often developed with very low computing power as a complex system is not necessary to perform most IoT tasks. Many IoT devices consist of a microcontroller, sensors and a GSM module, making it difficult to implement robust device encryption. When an IoT device communicates over the public internet, the unencrypted data it transfers is easily susceptible to attackers. By implementing a VPN between the IoT application server and the EMnify EMcore platform, all traffic is fitted with strong encryption before it is sent over the public internet. Additionally, this process is completely transparent for the mobile device and does not require special hardware or any additional configuration on the IoT device itself.
To explore what security can mean for IoT devices, we will explore the example of traffic signal hacking in Michigan.
A case for improved security: Urban Traffic Cameras
In 2014, a team of researchers at the University of Michigan School of Computer Science and Engineering sought to investigate potential security flaws in a municipal network traffic signal system. The team, working with the proper authorities to ensure public safety, was able to gain access to a traffic signal system that controlled nearly 100 intersections, showing successfully a variety of security failures that existed. Although the research points to a systematic lack of security infrastructure, the greatest security breaches were found in the connectivity between the traffic lights and the traffic controller. This breach allowed the research team to change the color of the traffic signal on command.
Hacking of this nature could greatly jeopardize the public safety, cause infrastructure & economic disruptions and overload municipal systems. In addition to other security precautions, a VPN would protect wireless commands going over the public internet through an encrypted tunnel. The VPN could also lock down the camera to only receive commands from an authorized IP addresses, separating it from the public internet. This ensures that even if someone did break into the traffic system, lights would remain unresponsive to outside control.
Optimization of Data Management
By using a VPN you are gaining transparent network access to your IoT devices in addition to security advantages. This means network connection can be initiated from your application towards the device and there is no limitation of network protocol that can used, because no network address translation is needed. A VPN allows you to “pull” data from IoT devices, instead of waiting for those devices to “push” the data to you. In short, this results in an optimization of data usage as data can be requested on demand when it is really needed.
To explore how the optimization of data can save money and resources, we will look at the example of a remote temperature sensor.
A case for data optimization: Wind Turbine Engineering
A German mechanical engineering company builds wind turbines that are sold worldwide. The company uses an embedded SIM card to track these machines geographically, and to send alerts for a number of events. These include energy output and running time, but most importantly the company receives information regarding any mechanical malfunctions.
The engineering company does not need to access the data each day, however must have connectivity to the turbine to run diagnostics when a malfunction occurs. With a VPN properly implemented, the company is able to remotely communicate with the machine and securely query diagnostic data when it is needed. A VPN enables when the company initiates connectivity with the machine, how much data is needed to assess the malfunction, and the connection is instantly available on any workstation connected through the same VPN. The engineering company is utilizing a VPN to both manage efficient data usage and ensure immediate access to their remote machinery.
No need for private APNs
The APN defines the gateway from the mobile network to the public internet. Traditionally private APNs are used to assign static IP addresses to devices that connect to the private APN - so that these devices traffic can be bundled, integrated into their own private network, and the devices remotely accessed. emnify assigns already static IP addresses within private subnets that only belong to the customer. The VPN is then only established between the customer device and application subnet. A private APN does not provide any additional advantage.
VPN Options
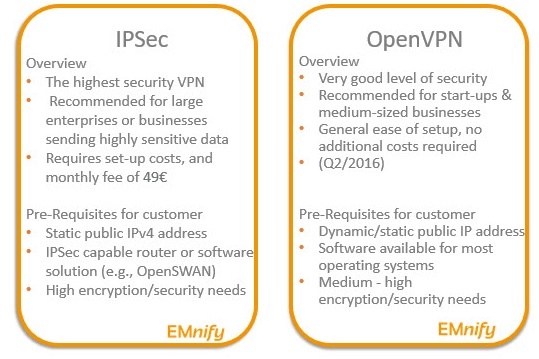
emnify offers 2 different VPN options for customers, IPSec (available to basic, professional and enterprise customers only, and requires an additional fee) and OpenVPN (available in Q2). The one you select is largely dependent on the size of your business and the demands of your actual application. In the most general terms, IPSec is the highest security VPN, closely followed by OpenVPN.
IPSec
Internet Protocol Security (IPSec) sets up a tunnel from a remote device to a central business server. It is designed specifically for internet traffic and ensures private, secure communication over the public internet by cryptographic security services.
IPSec is recommended for large, global enterprises, especially when multiple peers and security layers are in utilized. IPSec requires a static IP address, and technical resources to implement. Larger enterprises are often those with the needs and resources to meet these barriers. A harder technical set-up also makes this VPN option the only one that emnify charges to implement and maintain, and is only available for the Basic Edition of the emnify platform and higher.
The other strong case for IPSec exists when dealing with data of a very sensitive nature such as the transfer of personal identification information.
OpenVPN
OpenVPN is an open-source software that utilizes the security protocol SSL/TLS. It has strong feature and is know for ease of implementation. It allows customers to authenticate each other using a pre-shared key. OpenVPN works in a client-server mode, meaning OpenVPN users connect to the OpenVPN server and from there have full access to the internet.
OpenVPN is recommended by emnify for most use cases from start-up through medium-sized businesses who require a high level of security, but are comfortable with the flexibility of an opensource software. Users of OpenVPN can have either dynamic or static IP addresses, and the software is increasingly becoming available on most operating systems.
To set up a VPN with emnify, contact our customer support at support.emnify.com and we can help you during this process.
Get in touch with our IoT experts
Discover how emnify can help you grow your business and talk to one of our IoT consultants today!

emnify
The content team of emnify is specialized in all things IoT. Feel free to reach out to us if you have any question.