

Businesses worldwide spent $1.5 billion on IoT security in 2019. An incredible number, especially given we are just beginning the IoT journey. When it comes to connecting devices via cellular IoT, the selling-point is typically the data and derived insights – this is where the customer sees real value, more so than in any security benefits. That said, IoT solution providers not taking security measures into consideration are risking significant revenue and reputation loss in the event of a security breach – both for their own business as well as their customer’s business. In the worst cases, the harm done from one security breach will far outweigh any previously created customer value. Businesses that can explain and demonstrate their security concepts will gain a competitive advantage.
Why are hackers focused on IoT?
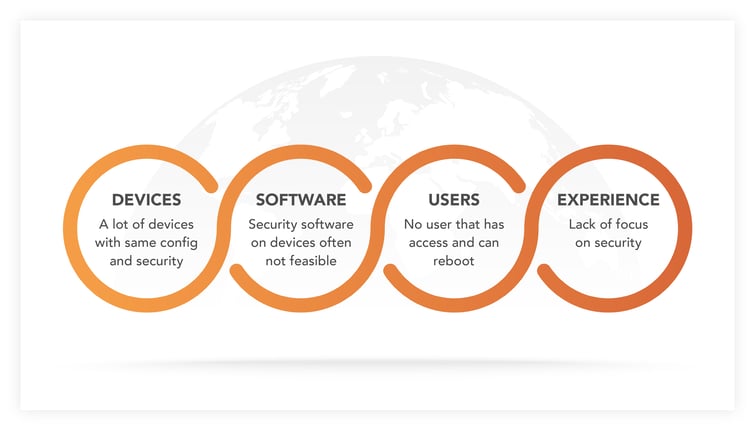
IoT attacks increased by 900% in 2019. So, why are hackers increasingly targeting IoT devices? There are several explanations:
- Lack of security software on the devices: Opposed to regular computers, IoT devices do not have a firewall, or virus scanner.
- Less experienced device producers: The businesses usually come from the industry vertical and often are lacking the IT security expertise of server / computer manufacturers.
- Multiple devices with the same security mechanisms: Once an attack works with one device it will work with thousands.
- IoT devices are out of reach: device owners deploy their machines remotely. Often an owner won’t realize that the devices have been compromised until it is too late. Once an attacker has control over a device, it could run all day long before being physically shut down by the owner.
Who are the attackers and what are their motivations?
- Amateur hackers and script kiddies – usually their objective is fame among their peers, either by targeting a high-profile victim or by demonstrating an ability to infect many devices in a single attack.
- Governments / intelligence organizations – acting in the safety of their citizens, intelligence agencies attempt to secure access to important information.
- Political interest groups – they attack organizations that they think are morally corrupt. Examples are groups like anonymous.
- Criminal businesses – organizations that take advantage of vulnerabilities within the target to generate revenue for themselves.
The criminal businesses mentioned above are typically set up as ordinary businesses and are especially relevant in the IoT domain. Their objective is to gain control over a large number of IoT devices and make money out of them, often in one of the following ways:
- Selling Distributed Denial of Service attacks – like webstresser.org (more information via Forbes)
- Using devices for Bitcoin mining (more information via CNBC)
- Blocking the device operation until the owner pays a ransom (ransomware)
How do the most common IoT attacks work?
Mirai
The most common IoT attack today is the Mirai malware, which originated in 2016. The malware scans the public internet for IoT devices and tries to establish a remote telnet connection using a list of common factory default username and passwords. As soon as one device is infected, the malware begins scanning for more victims. All devices become part of the Mirai botnet which is then steered through the attacker’s command and control center. The attackers then execute a DDoS attack, on behalf of their customers, to a target destination in order to take down the servers of the victims.
Stuxnet
The Stuxnet computer worm was first uncovered in 2010. The malware first injects Microsoft Windows machines exploiting zero-day exploit or outdated OS versions; initially it spread over USB flash drives. On the Windows machine it looks for the Siemens Step7 software that controls the Siemens programmable logic controller (PLC). With the Step7 software it then installs itself on the IoT device and takes over control. Stuxnet once targeted Iranian facilities and reportedly severely harmed the Iranian atomic program.
Silex / Brickerbot
While Brickerbot was discovered in 2017 – Silux appeared in 2019 – but with a common attack pattern. Like Mirai, the software scans the public internet and tries to log in to the IoT device with default and weak login and password combinations. After infection, the software overwrites all data and deletes the network configuration, which makes the IoT device unusable, unless someone can physically get a hand on the device.
Recommended countermeasures to guard against attacks
As seen in the Stuxnet attack, IoT devices in the same network as other machines can be impacted by the vulnerabilities of those other machines. To avoid this, using a dedicated network infrastructure is recommended, instead of using shared LAN or Wi-Fi networks. Alternatively, using cellular communication that separates the communication of the different machines is also preferred.
The Mirai and Silex / Brickerbot malware shows the value of having random and unique log-in credentials for the different devices – this could have prevented the above attack. While the devices allowed for remote access by their owners, the access was granted via unsecured public internet. A more secure way to get remote access to IoT devices is to use IPSec or Intra-Cloud Connect, avoiding the exposure of public Internet.
One way to prevent attempts to steal remote access to IoT devices, as well as completely block attacks, is to use a cellular firewall. With a cellular firewall, devices are only permitted to communicate with a defined subset of IP addresses. The firewall itself is not located on the individual devices, rather on the cellular connection – out of the attacker’s control.
To find out more about what cellular IoT best practices to consider for your business, download our new whitepaper.
Get in touch with our IoT experts
Discover how emnify can help you grow your business and talk to one of our IoT consultants today!

Christian Henke
If you want to understand how emnify customers are using the platform Christian has the insights. With a clear vision to build the most reliable and secure cellular network that can be controlled by IoT businesses Christian is leading the emnify product network team.



