

At EMnify, a security-first approach is the foundation of the development of our platform features. This is reflected in our solutions which enable TLS on A2P SMS, the integration of your IoT devices with your VPC via Cloud Connect, and multiple software and physical measures undertaken to prevent SIM misuse. The addition of configurable DNS settings for device groups allows for end-to-end control of the networking settings of your devices. Aside from providing further options for using alternative public DNS services, device fleets can now be restricted to use private DNS services which do not expose DNS query logs or internal server IPs, and may be configured to drop internet access for hardened security-first IoT infrastructure.
Background on DNS
Domain Name System (DNS) is a naming system and directory for computers connected to the Internet. Machines are assigned unique IP addresses so that other machines can communicate back and forth reliably. When internet users browse online, the domain names requested (emnify.com or even firmware-update.example.com) need to be translated to the IP addresses used by the hosting servers so that a browser or client can retrieve the relevant data. DNS performs this translation of the text-based domain names to the machine or server IP address so that users do not have to memorize numeric IPs. For this reason, DNS is commonly referred to as 'the phonebook of the Internet'.
Enhanced security with a private DNS service
The main advantage of a private DNS service for an IoT fleet is that devices will not be able to resolve IP addresses for any public domain names. If DNS lookup is simply dropped for non-approved or public domains, IoT devices cannot request malicious resources and already-infected devices would typically be rendered useless for use in a DDoS attack. Incidentally, this can also prevent unintentional data consumption in cases where misconfigured devices request the wrong resources.
If a customer application server communicates often with IoT devices, it might not be desirable to add the IP address of this internal service to public DNS servers. Poorly-maintained DNS servers are occasionally vulnerable to a method known as cache poisoning where cached records are altered to point to an IP address an attacker controls. If we consider the danger this poses with domains such as firmware-update.example.com, a private DNS service can provide data integrity by ensuring that IoT devices receive authentic software upgrades via the correct update server. The private DNS server becomes the only authoritative server capable of responding to the update site domain name in this case.
For customers who already have infrastructure deployed to a cloud provider, the DNS services like Route 53 on AWS, for example, can be configured so that only devices within your VPC can use it for private DNS resolution. Using EMnify's CloudConnect, the DNS service of your cloud provider will only respond to queries from IoT devices when they originate from within a VPC that is authorized. EMnify supports attaching the VPC of your IoT devices with your existing VPC via CloudConnect on AWS, Google Cloud Platform, and Azure.
Configure DNS settings for EMnify IoT devices
EMnify now supports setting custom DNS configurations in Service Profiles which allows groups of devices to use the specified DNS configuration. Users can add primary and secondary nameservers via the EMnify API with UI components to follow soon.
A POST request to /api/v1/dns will create a new DNS config:
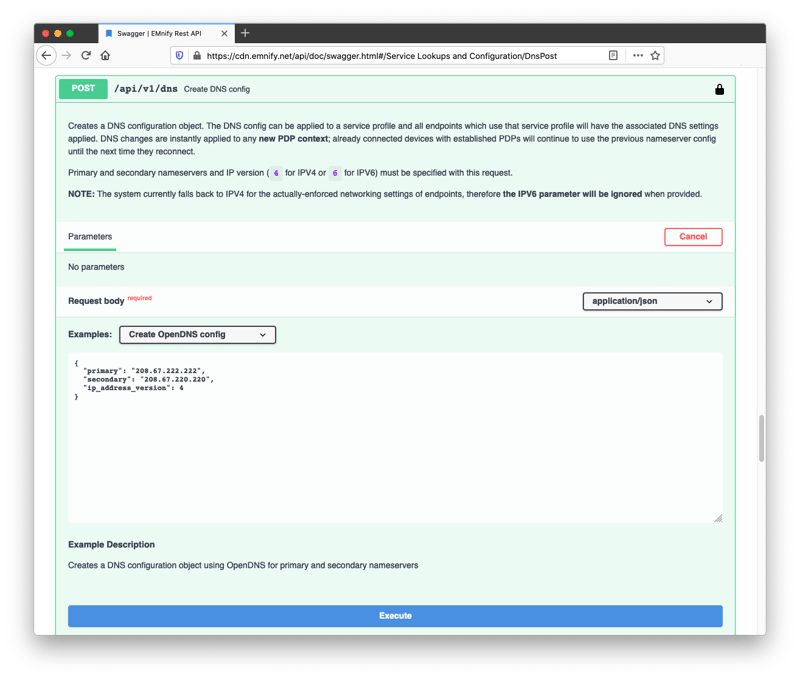
The DNS configurations can then be listed via a GET request to /api/v1/dns.
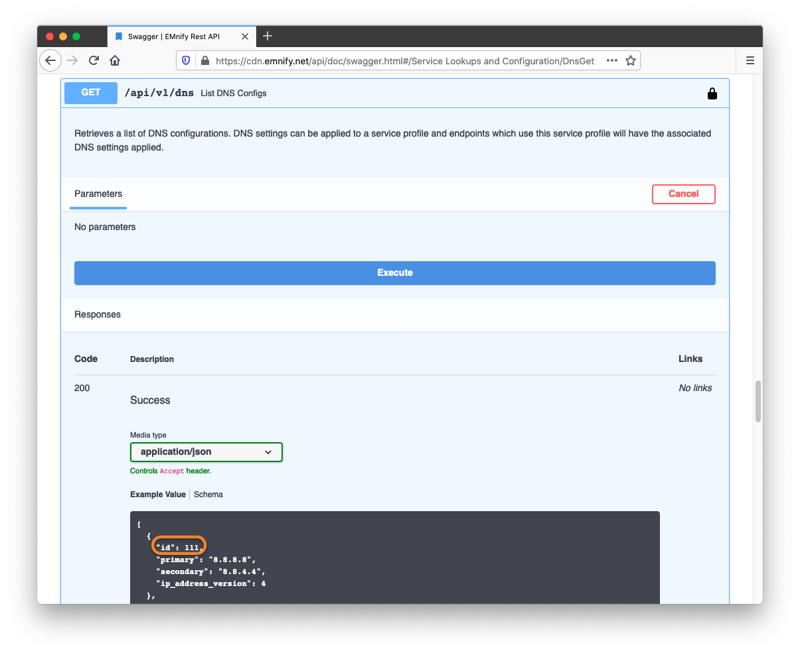
The IDs of these DNS objects are added to existing or new Service Profiles. To list existing Service Profiles, perform a GET to /api/v1/service_profiles and copy the id of the profile you would like to update:
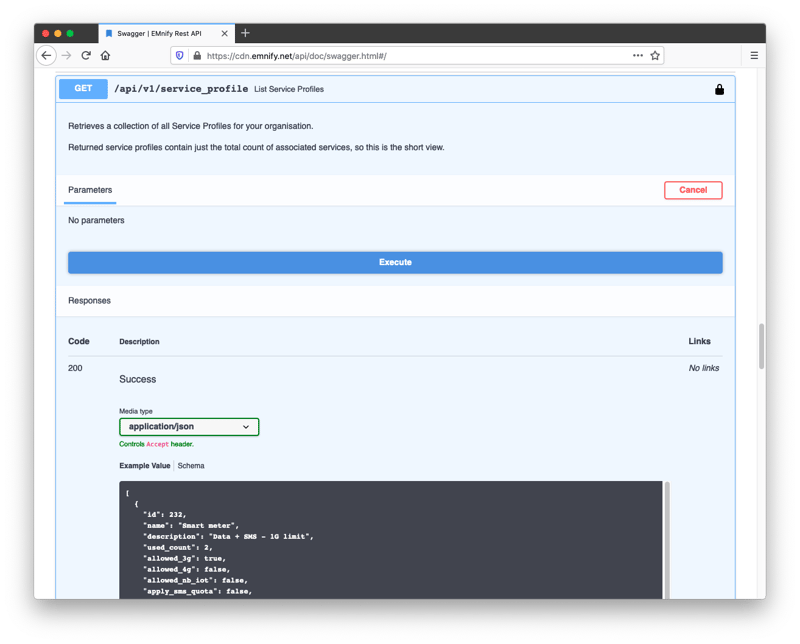 Paste the numeric profile ID into the parameter for the PATCH /api/v1/service_profile, select one of the example DNS settings (or provide your own), and click execute:
Paste the numeric profile ID into the parameter for the PATCH /api/v1/service_profile, select one of the example DNS settings (or provide your own), and click execute: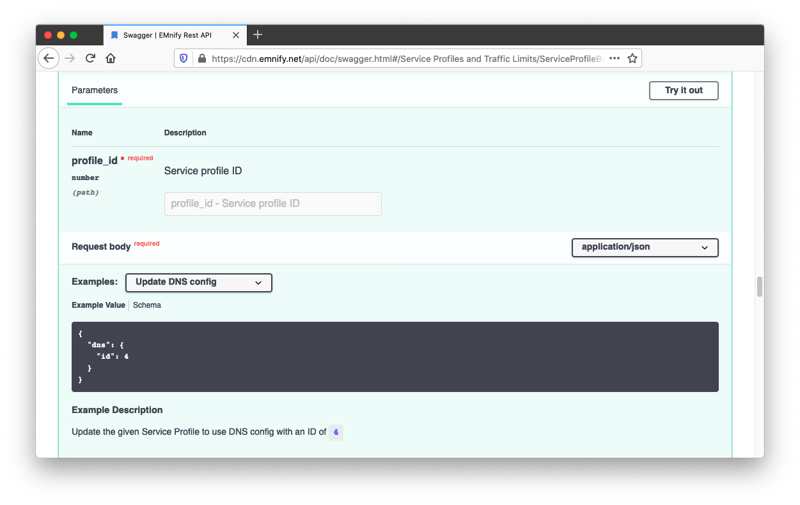
The networking settings of IoT devices using this Service Profile will be updated on their next data connection to use the new DNS configuration. The Swagger documentation provides public DNS servers known for their resilience and quality of service in the examples:
OpenDNS is one of the largest free providers claiming 100% uptime and malicious content filtering enabled by default.
Cloudflare offers low latency of requests without logging IP addresses and consistently come out on top as the fastest DNS provider on the market.
Google Public DNS used for reliability and speed, offering full IP logs for 48 hours on their platform.
Comodo Secure DNS provided by a security firm with advanced options for filtering malicious content on the DNS level.
Summary
With the addition of DNS configuration via Service Profiles, users can quickly configure the networking settings of device groups in bulk.
Private DNS benefits:
- Enable the use of internal domain names
- Manage the lookup of domain names to restrict access to the public Internet
- Troubleshoot networking errors on the DNS level
- Add better stability and reliability to DNS
- Reduce attack surface of your infrastructure by keeping DNS lookup internal
Custom DNS with CloudConnect and IPsec benefits:
- Private DNS services as a managed service by cloud providers which are not accessible over the public internet
- Full control of domain resolution per service with additional logging
- Device networking has lower latency and is fully internal to a VPC - IoT devices reside on the same networks as DNS and application servers
More details on the setup of DNS configuration can be found in the EMnify KnowledgeBase article for DNS configs.

Joseph Johnson
Joe is an experienced engineer in the field of telecommunication systems, applications and IoT. He is currently supporting the sales team for all things technical and is a valued member of the emnify family.




